Evilnum Malware: A Backdoor to Target Cryptocurrency and Financial Entities for Data Theft

EvilNum is a backdoor malware that can be used to steal data or load extra payloads with a number of intriguing components to avoid detection and alter infection paths based on well-known antivirus software. TA4563 is a threat actor that uses EvilNum malware, particularly in operations that support foreign exchange, cryptocurrency, and the Decentralized Finance (DeFi) industry. The most recent activities use updated TTPs and send victims spear-phishing emails with Microsoft Word, ISO, and Windows Shortcut (LNK) files as email attachments.
The malicious document is sent to the victim through a spear phishing email. As the victim opens the downloaded document, two macros are fetched from the attackers-hosted domain, displaying decoy content. The first one is used to execute PowerShell scripts and decrypt PNG files and further restart the attack chain. Another macro is used to load the C# code and send screenshots to the C2 server.

As the malware tries to call multiple executables on the host machine, the applications on the victim machine execute depending on the type of anti-virus that is found to avoid being detected by them. Two encrypted blobs are present in the second payload that is decrypted into an executable file(hpfde.exe) and a TMP file(devXYXY5.tmp) which loads a shellcode and a decompressed PE file. This acquired backdoor can be further used for reconnaissance, data theft, and payload deployment.
The malware is evolving with more advanced features every passing year. At the end of 2021, it was only seen attempting to deliver the Microsoft Word documents with a financial theme to communicate with the domains to get the LNK loader with WScript to load the payload and JavaScript payload on the target host. In early 2022, the malware further attempted to deliver multiple OneDrive URLs with ISO or .LNK attachments as a variation on the original email campaign. The evolution has led to the group delivering Microsoft Word documents to download a remote word template that generates traffic between the actor-controlled domain and the users’ host to launch the EvilNum payload.
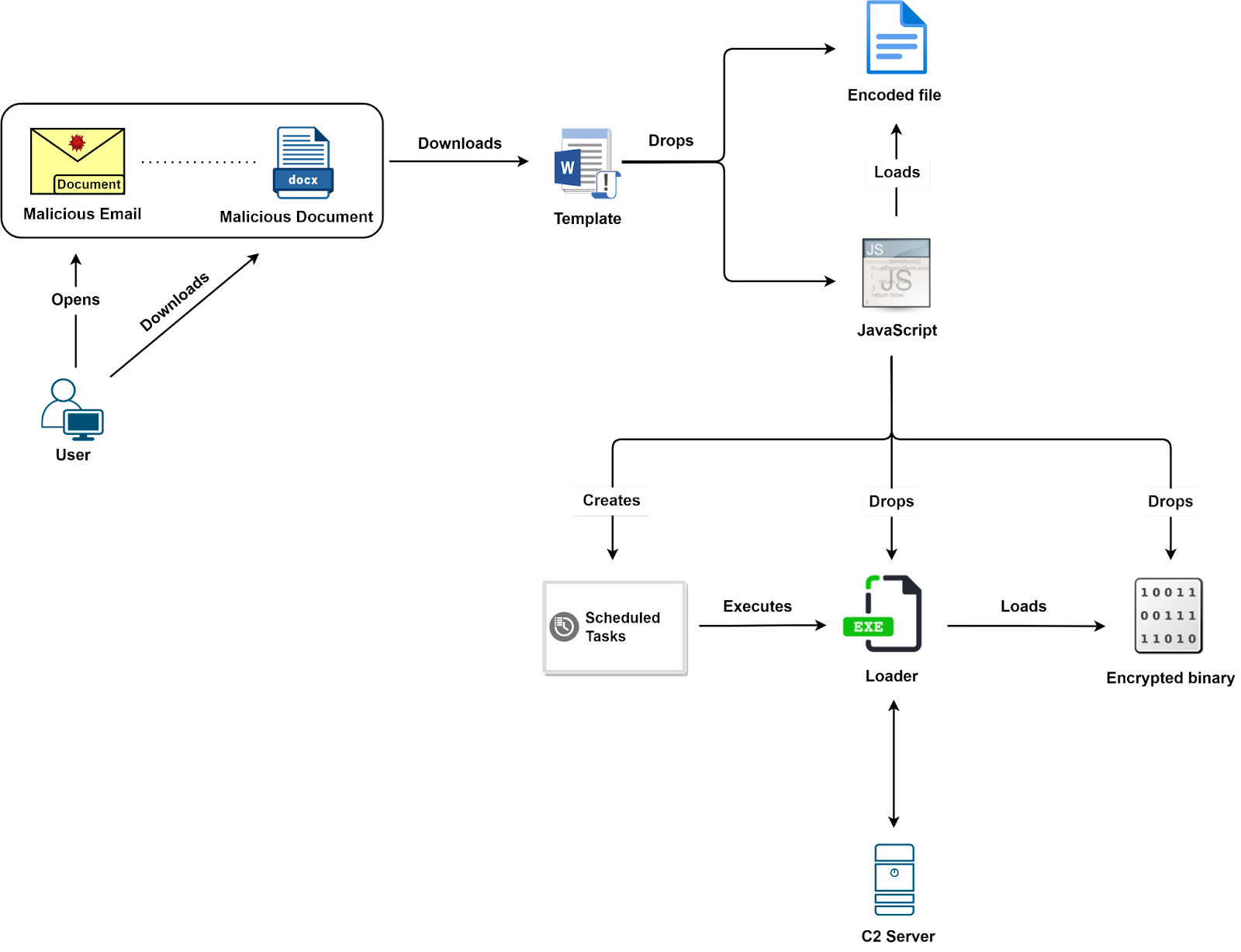
The actor aims to gain information on both target companies and their customers' financial information. The group is capable of securing information from spreadsheets and documents, the institutions' software licensed and trading credentials, browser cookies, and session information, along with email credentials and credit card information. Additionally, in recent cases, through the payload, the group has also gained access to the VPN configuration of the institutions’ networks.
Workaround
Malware is still being actively developed, and a persistent adversary will keep changing its tactics to compromise systems. It is recommended to train employees to identify and report suspicious emails. The targeted organization should make sure that the use of container files such as ISO and LNK is restricted and that the RTF files are blocked from being downloaded or accessed from Word.
References
https://www.zscaler.com/blogs/security-research/return-evilnum-apt-updated-ttps-and-new-targets