Evolved BumbleBee Backdoor
Introduction
Bumblebee is a backdoor with unique modular architecture and has a string embedded in the malware. Previously, it was used to track keys and clipboard content, but now it has evolved to execute legitimate executable and is a controller application that expands its capabilities. It is similar to the BookWorm backdoor that abuses legitimate executable to load malware and uses encryption modular structure and C&C communications with the use of similar network protocols.
Technical Analysis
The advanced version serves as a modular backdoor with two applications a server and a client. Its backdoor functionality allows it to take control of the machine using the server module where the client application is deployed on the victim device. It uses a layer-in-layer architecture with modules divided into three main parts as files a legitimate executable (XcrSvr.exe), a side-loaded DLL (XecureIO_v20.dll), and a shellcode binary file (ore) in the file system. The shellcode “ore” is the main component of the backdoor after the layered loading of executables. XcrSvr.exe is used to load XecureIO_v20.dll, which verifies whether or not it is a parent process and directs execution flow to the malicious code to patch the entry point of XcrSvr.exe.
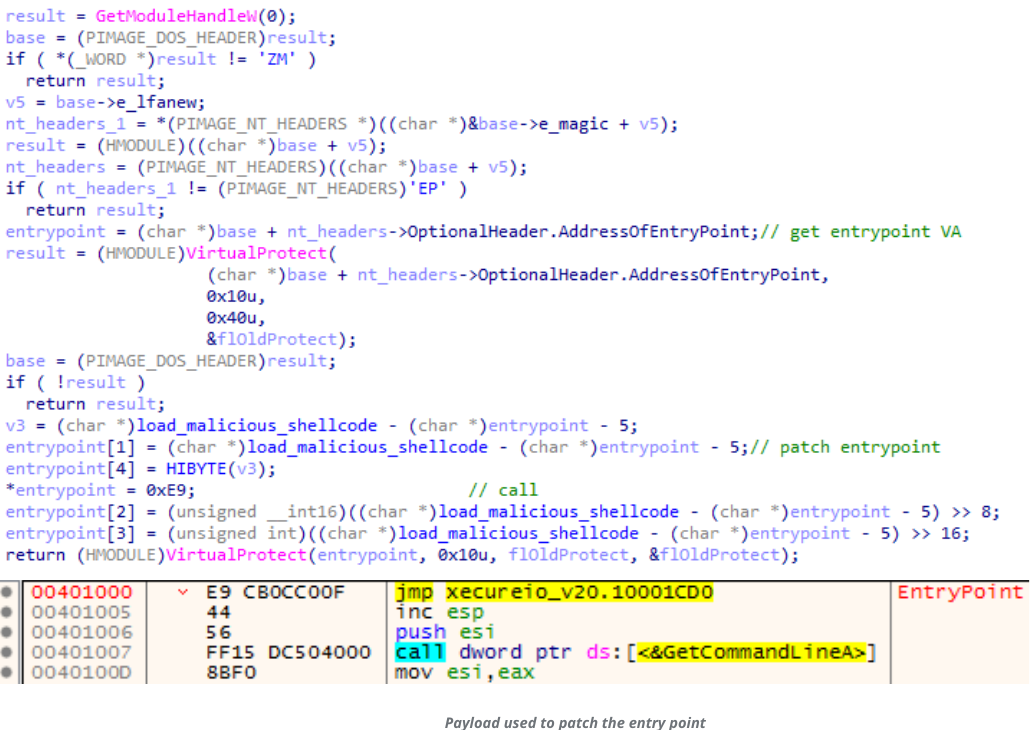
The launcher is used to launch the modules for installing and maintaining the resistant presence initially to load the modules. So, along with it, the launcher also loads the parent process “XcrSvr.exe.” and is directed to process with malicious code directly. According to the analysis, after the installation of the loader, the DLL retrieves a value(ProductID) from the registry key(“HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Registration”) and uses it to decrypt the encrypted payload loaded during the installation.
As bumblebee has grown to expand its exploitability, it works as a complex client application that runs across a server application of the malware and acts as a controller. The client application running in the user system establishes communication with the server application to display collected client device information such as computer name, external IP address, geographic location, OS, CPU, and memory. Bumblebee specifically uses the modular framework to involve malicious codes to perform actions that lead to stealing keystrokes and clipboard content. The layer formulation and structure provide the bumblebee the flexibility to develop additional modules, making it difficult to analyze or track.
In terms of network communication, Bumblebee sends an HTTP POST request to communicate with the command and control server. Through the channel, the client application sends the information in an encrypted format. The information is also compressed using the LZO algorithm and encrypted using RC4. In addition to that, Bumblebee uses a CRC32 checksum to verify the data. Its persistent nature comes with the adoption of different techniques, such as the continuous misuse of registry run keys to execute malware immediately after the system boots. It also works to create Windows services to consistently execute malicious payloads along with login scripts.
Conclusion
As of recent analysis, Bumblebee has only been deployed in China, but with the complexity and accuracy of its work, it is sure to expand its horizons. With the use of a modular framework and as the additional modules are easily integrable, this newer version can grow to be quite heinous. However, using backdoor protection systems and applications along with quick detection and layer protection functionality can help prevent the client system to a certain extent.