Follina: A zero-day vulnerability in Microsoft Office that supports code execution

A zero-day remote code execution vulnerability was identified and shared by Nao_sec through Twitter, which reported finding a malicious Word file designed to execute arbitrary PowerShell code. The vulnerability has been tracked as CVE-2022-30190 and has the potential to take control of the system, escalate privilege levels, install programs, view, change, or delete data, and even create new accounts. The name Follina was given by one of the first researchers Kevin Beaumont, as the malicious sample on the file references 0438 which is the area code of the Follina in Italy.
Initially, Follina was described as a Microsoft office Vulnerability but later it was stated to be affecting Microsoft Support Diagnostic Tool (MSDT) and collected information that was sent to Microsoft support. The exploit is confirmed to work against Office Pro Plus, Office 2013, Office 2016, Office 2019, and Office 2021 and affects Windows 7, Windows 8.1, Windows 10, Windows 11, Windows Server 2008, Windows Server 2012, Windows Server 2016, Windows Server 2019, and Windows Server 2022.
The exploit
In comparison to other attacks where word files are used, the attack does not rely on macros which makes it work even when they are disabled. It is done through MSDT (Microsoft Diagnostics Tool) and other Microsoft Utilities mainly Microsoft Word.
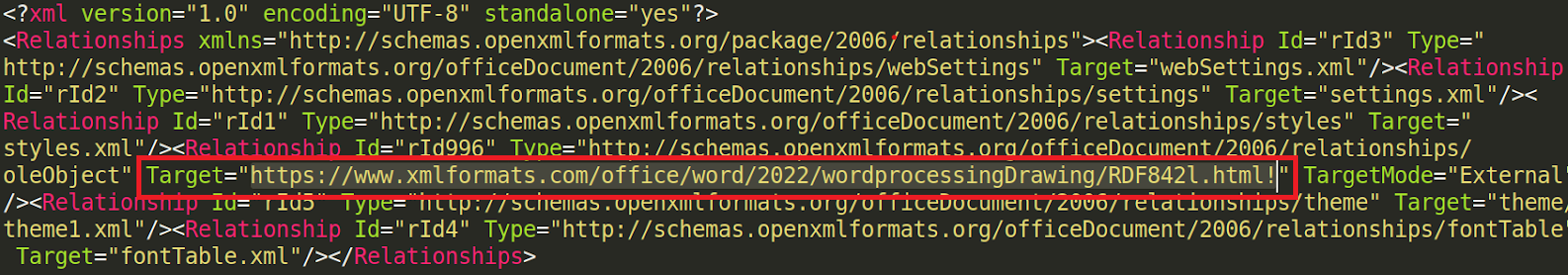
In the process of exploitation, the word document is unzipped to extract the component that could carry the exploit. The zip contained several files in which a file named ‘document.xml.rels’ contained a URL within it. The URL referenced to have contained an abettor HTML file which consisted of a hefty number of unnecessary characters that were capable of setting off the exploit. The native package in ms-msdt invoked certain parameters that included PowerShell syntax embedded within $().
That worked in extracting the payload from the file which is decoded and displayed that the script consisted of a cmd.exe that is captured as a variable which displays certain processing such as starting the hidden windows to call msdt.exe, loop thorough files that are inside the RAR file, store encode and decode CAB files and execute the rgb.exe file. The rgb.exe file is considered nobly threatful for allowing the threat actors to execute code with just a single click. The attack components were hidden inside the Microsoft word document without macros, they can run remotely hosted code.
As stated by John Hammond in his analysis of the exploit, the attack is variant and can be executed in various forms and has a high scope of intrusion. The triggering payload can reach remote locations, invoke untrusted binary, and create a connection that even allows bad actors to achieve a hash of the victim’s windows password. He also mentioned that once this code is detonated, threat actors can elevate their privileges and potentially gain ‘God Mode’ access to the affected environment. Summoning that the fact how the exploit works in running the code under the user’s account and navigates towards the malicious document indicating that it is capable of accessing and escalating the user privilege.
In summary, the exploit simply works when the official document is opened it calls the Microsoft diagnostic tool which further calls the PowerShell which executes codes that downloads malicious programs or runs commands to upload files to the target system or the internet.
Workarounds for the vulnerability
Certain remediation and guidance were released for the vulnerability by Microsoft to address the issue after denying the severity for a consistent amount of time. Workarounds that were released covered certain precautions like:
Disabling the MSDT URL protocol which helps prevent the troubleshooters from being launched as links throughout the Operating system. If the troubleshooter is still accessible, the registry key must be used to disable and restore them as per need.
As Microsoft Defender Antivirus uses artificial intelligence and machine learning to identify and stop unknown threats, customers are requested to turn on cloud-delivered protection and automotive sample submission to quickly identify and stop them.
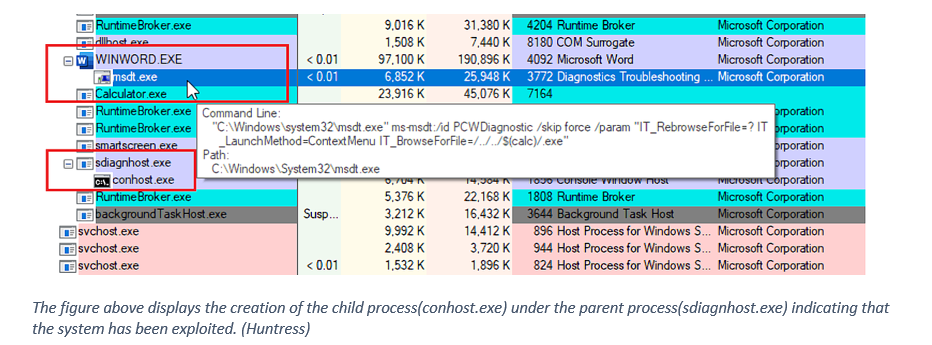
As the process of creating child processes is common among the malware strategy, Customers of Microsoft Defender for Endpoint can enable the “BlockOfficeCreateProcessRule” attack surface reduction rule, which prevents Office programs from creating child processes.
Under the use of inbuilt signatures for detection and protection of possible vulnerabilities, alerts are generated with indicative titles like ‘_Suspicious behavior by an Office application ‘_or ‘Suspicious behavior by Msdt.exe’ if Microsoft 365 Defender portal is working on the network.
The researchers have also suggested that the removable of the file type association for the Microsoft Diagnostics Tool can disable the file from executing and prevent the malicious code from targeting it to further carry on the execution. Overall, this malicious code simply set off as easily as Word doc even in preview mode, and if not patched in time the exploit is likely to be transmitted through email-based delivery soon.
References
huntress.com/blog/microsoft-office-remote-code-execution-follina-msdt-bug
doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e