615000+ Facebook Credentials Stolen – Large Scale Phishing Campaign

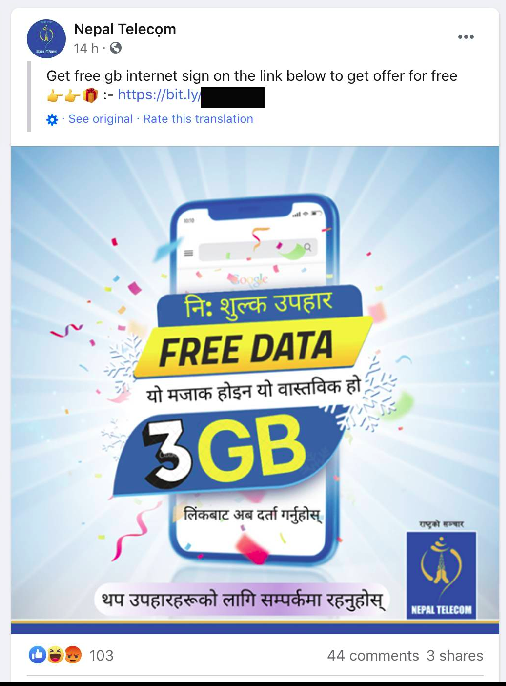
Threat Nix has uncovered a large scale phishing campaign using GitHub pages and targeted Facebook ads that has affected more than 615000 users. The campaign is targeting Nepal, Egypt, Philippines along with a large number of other countries. Our researchers first came across the campaign through a sponsored Facebook post that was offering 3 GB mobile data from Nepal Telecom and redirecting to a phishing site hosted on GitHub pages.
Campaign Operation
The campaign is using localized Facebook posts and pages spoofing legitimate entities and targeted ads for specific countries. As an example, the post we came across was targeted specifically for Nepal by using Nepali language and offering data packages for Nepal Telecom, local telecom service provider. The page that posted the ad was using the profile picture and name of Nepal Telecom and was almost indistinguishable from the legitimate page. We saw similar Facebook posts targeting Facebook users from Tunisia, Egypt, Philippines, Pakistan etc.
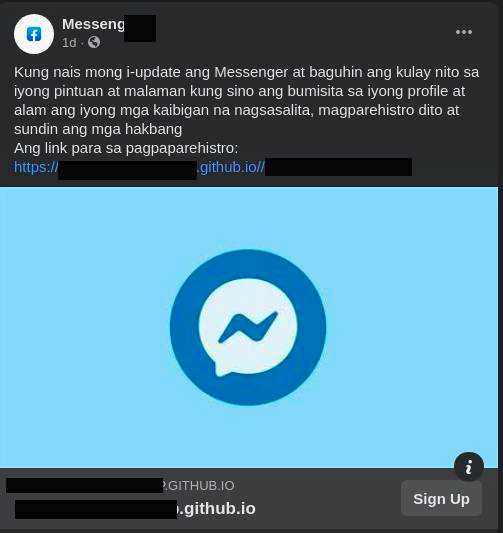
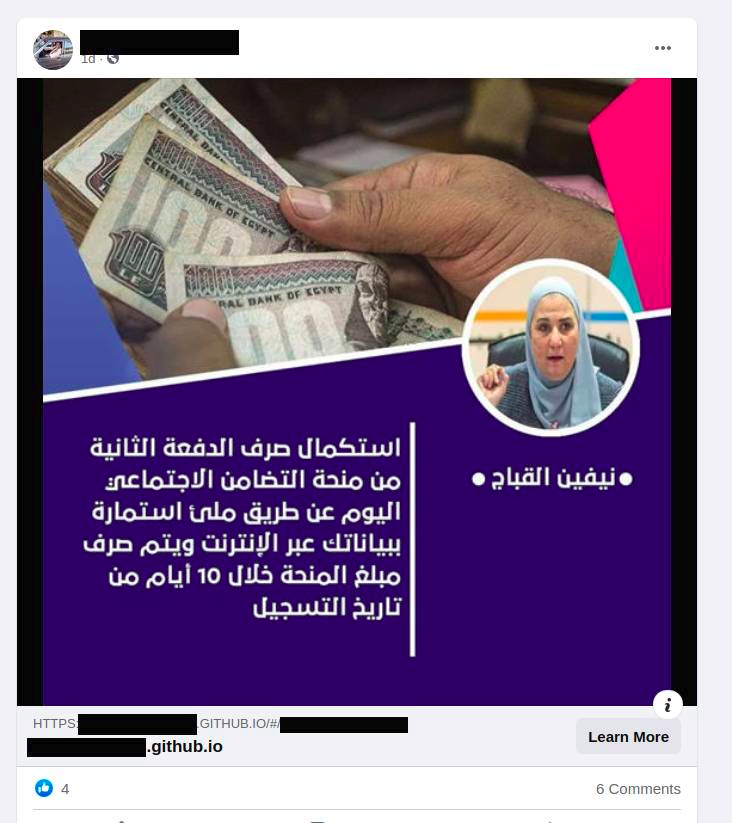
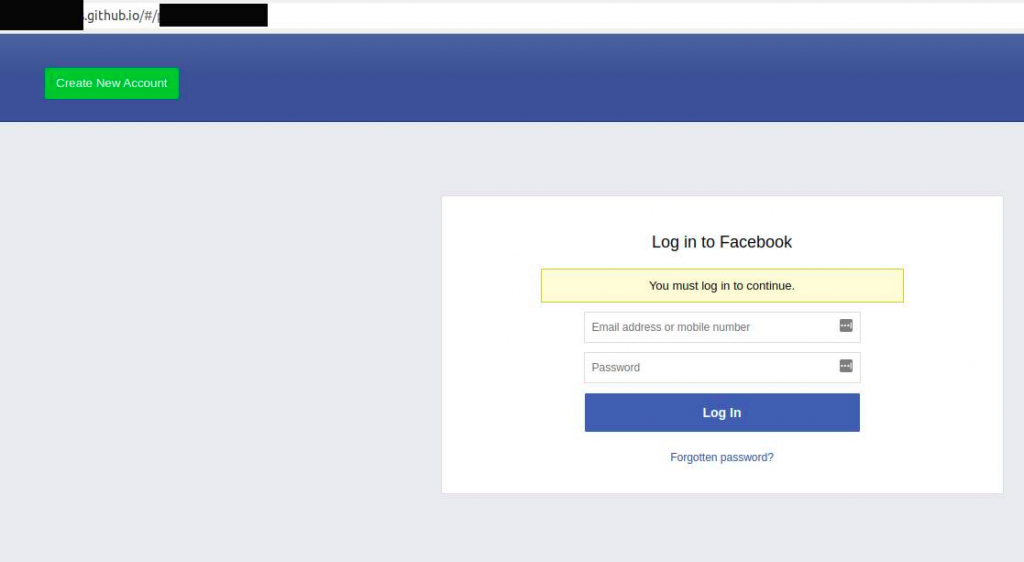
Links within these posts then redirected to a static Github page website that contained a login panel for Facebook. All these static GitHub pages forwarded the phished credentials to two endpoints one to a Firestore database and another to a domain owned by the phishing group.
While Facebook takes measures to make sure that such phishing pages are not approved for ads, in this case the scammers were using Bitly link’s which initially must have pointed to a benign page and once the ad was approved, was modified to point to the phishing domain.
We discovered almost 500 GitHub repositories containing phishing pages that are a part of the same phishing campaign. These repositories are created by a variety of recent accounts and some of the pages were abandoned and were no longer available on GitHub pages. The earliest these pages were created in GitHub was 5 months back but as some GitHub repositories were deleted so it is possible that similar tactics were used before that as well.
This domain being used in the campaign is behind CloudFlare was first created on April 3rd 2020 and is registered and hosted on GoDaddy. Four other domains were identified that are suspected to belong to the same group.
Affected Users
Following some digging we were able to gain access to those phished credentials. At the time of writing this post there appears to be more than 615,000+ entries and the list is growing at a rapid pace of more than a 100 entries per minute
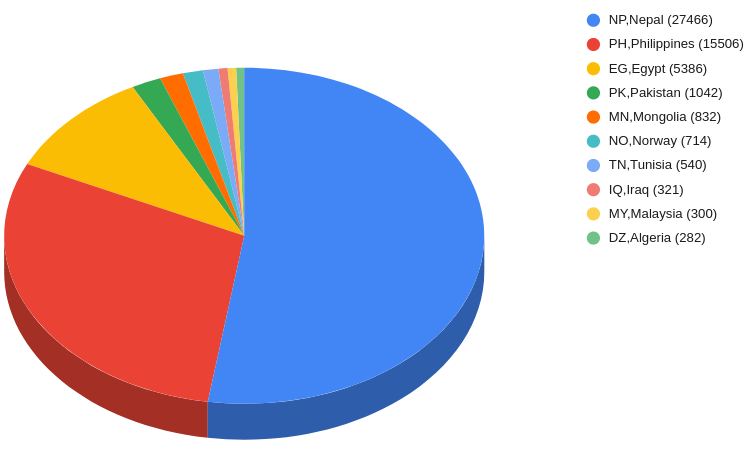
 Entries from more than 50 countries were seen in the leaked data. Taking a sample of the latest 50,000 data, the distribution of top 10 countries is as follows
Entries from more than 50 countries were seen in the leaked data. Taking a sample of the latest 50,000 data, the distribution of top 10 countries is as follows
Take Down Actions
We are working on taking down the phishing infrastructure by collaborating with relevant authorities as such we are withholding the information related to the domains until then. We will be providing further updates on our research once we further trace the scope of the campaign and the threat actor.
This seems to be a sophisticated large scale operation and we will continue investigating this further more. If you are willing to collaborate with us on the research please reach out to us
Threat Nix is a Nepalese security firm providing cyber security services to clients around the globe.