Maui Ransomware a Threat to Healthcare Organizations

As a spawn of Ransomware-as-a-Service(RaaS) amongst threat actors, Maui ransomware lacks several features but is getting closer to enclosing itself as a part of the group. The malware does not give ransom notes with recovery instructions to its victims like the others but has other potential that can disrupt services at multiple hospitals and clinics.
The ransomware has been acting up to grab the attention of large institutions such as the FBI since May 2021, as incidents relating to it affecting the HPH Sector organizations were reported.
According to the threat report presented by Stairwell, Maui has the capability to operate manually, and when executed, the remote operators will specify which files to encrypt and then exfiltrate the resultant runtime object.
Technical Analysis
The Maui ransomware is a privately developed encryption binary. Stairwell’s study of the Maui sample revealed that it was designed to be manually executed by remote threat actors. The actors interact with the malware through the command line and identify which files are to be encrypted.
The algorithms used to encrypt the files are Advanced Encryption Standard (AES), RSA(Rivest-Shamir-Adleman), and XOR. Each target file has a unique AES key and a custom header containing the file’s original path, allowing Maui to recognize previously encrypted files with copies of keys too.
Maui encodes each AES key with RSA encryption. It places the RSA public (maui.key) and private (maui.evd) keys in the same directory and further encodes the RSA public key using XOR encryption, which is generated through physical hard drive information. Maui stores the encryption output that is generated using ‘GetTempFileNameW’ command in a temporary file and creates a log (maui.log) for the encrypted files, exfiltrates them, and decrypts them using decryption tools by threat actors.
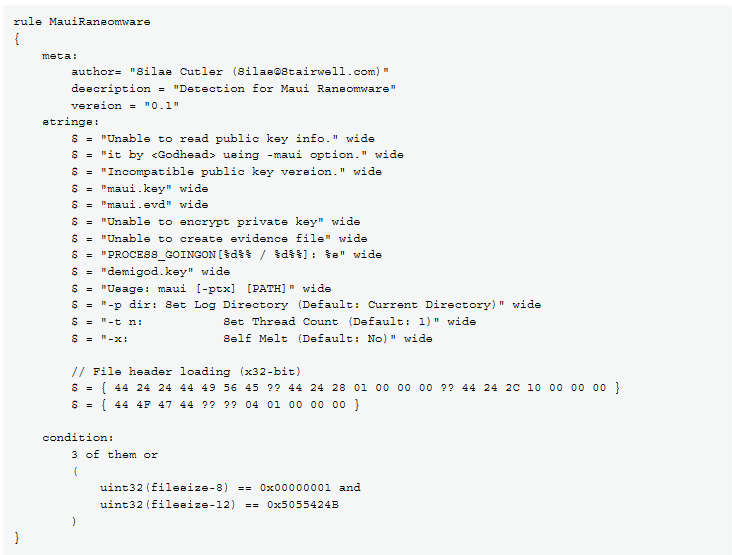
Further, the report also shows that the YARA rules of the ransomware could be easily accessed, and the public RSA keys that were stored in one of the Maui files can be extracted using python scripts.
Mitigation
Certain measures are to be taken for healthcare institutions to defend themselves from this type of ransomware. According to the FBI, CISA, and Treasury, limiting access should be given to data deployed using a public key or a digital certificate used to authenticate and ensure that those data packages are not manipulated during the transmission. Controls relating to authentication and accessibility should be applied by allowing only standard users to access the internal system.
In terms of communication-channel security, network devices such as firewalls should be used to protect the data (health information), and network interfaces should be disabled as much as possible. If needed, strong passwords and encryption can be set on them. Monitoring tools should be used, and internal data management and storage policies should be reviewed regularly. In the case of future threats, organizations should prepare themselves by maintaining offline backups of encrypted data and an incident response plan.
Additionally, it is good to regularly update systems, software, and hardware. This, along with anti-virus and anti-malware software, should be done. Moreover, secure networks should be used to prevent external network attacks with email banners to the messages that come from outside.
Resources
https://www.ic3.gov/Media/News/2022/220706.pdf
https://stairwell.com/wp-content/uploads/2022/07/Stairwell-Threat-Report-Maui-Ransomware.pdf