Nerbian RAT luring through email; A trojan with anti-detection and anti-analysis capabilities

A novel malware variant was attached to emails with embedded malicious capabilities and was spread leveraging the Covid-19 theme through multiple industries in Europe. The email claimed to represent the World Health Organization (WHO) giving vital information regarding Covid-19 safety. Researchers at Proofpoint named it Nerbian RAT based on its functionality. It is a trojan consisting of multiple anti-analysis components, complied for a 64-bit system, and works using multiple open-source Go libraries. With its subsequent data analysis and easy-to-use feature Go is consistently used by threat actors.
Observation of the email indicators and attachments clearly showed that the email was a phishing mail. According to the resources, the malware spread through the victim’s computer using the attachments sent in the email. There are additional logos from the Health Service Executive (HSE), the Government of Ireland, and the National Council for the Blind of Ireland (NCBI) on the document. The attachments on the email were word documents and compressed rar files.
Process Flow
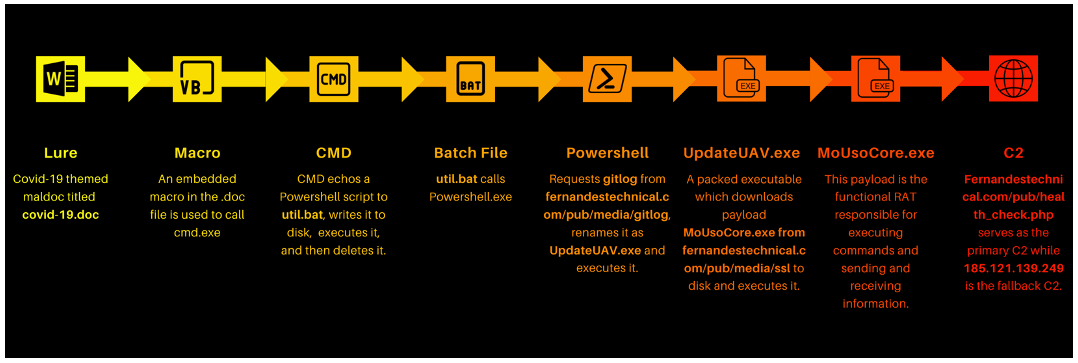
Technically, the complexity in its processing comes along with the number of features the malware carries. As the victim opens the attachment, it enables the macros on the document. The document executes the macros and drops a batch file in PowerShell. The dropper UpdateUAV.exe is a payload written in GO language. The file downloads and works as an executable in the targeted system. On an hourly basis, the dropper works to start the RAT payload as a scheduled task. It persistently attempts to download SSL (Secure Socket Layer) executable and names it MoUsoCore.exe. As a functional RAT (Remote Access Trojan), the payload works in executing commands that send and receive information for the attacker’s system.
Features
The RAT can be configured with only the functionalities that are necessary by its operators and others if required.
- It is capable of capturing keystrokes and writing them in encrypted format into a rev.sav file.
- It uses existing Go codes for screen capture on the different operating systems.
- It communicates via SSL to avoid being tracked down by network scanning tools.
- It aims to steal confidential data and works in an undetectable manner.
- The executable file UpdateUAV.exe used in it does not work in a virtualized or sandboxed environment and makes sure that the malware has enough time to perform its operations.
The anti-analysis technique examines the process list for any reverse engineering, debugging software, memory analysis, and memory tampering detection programs in the system. It also works to look for MAC addresses that are suspicious and analyze the WMI strings to determine if the disk names are correct. It even tests whether or not the executables are being debugged. Most of the functions of both the RAT and the dropper are referred from the GitHub repositories which makes them easily exposable.
Mitigation
It is highly recommended to apply proper email security measures to help prevent phishing emails from reaching the end-users. Thus, security controls such as anti-malware, anti-virus scanning, sandboxing, and anti-phishing solutions must be implemented. Providing proper phishing awareness campaigns and training to the end-users and maintaining a proper endpoint security control such as Endpoint detection and response (EDR) can help prevent such malware to affect the system. An endpoint detection and prevention system can be a helpful asset too. Using such systems detects abnormality and sends an alert upon the detection. If possible centralized control of external network usage for downloads and uploads can also be implemented.
Overall, the malware performed a three-stage act where the malicious document was used as a phishing lure, in addition to the dropper being downloaded to perform anti-reversing and VM checks and the Nerbian RAT working as an encrypted configuration file that ensure data to be transmitted in the encrypted format to the C2 server.
References
https://cyware.com/news/nerbian-rat-spreads-via-emails-in-ongoing-attacks-39023cc1