PDF malware tricking detection and sneaking through emails to infect systems

While most the users normally face malicious email campaign attacks in a form of a word document recently a campaign was discovered that used malicious PDF files to hide and spread keylogger malware. The campaign was discovered by researchers at HP Wolf Security with an intent to dupe victims with an attached PDF file which consisted of information about remittance payment.
The research document so published purported that the attackers used an old office bug to propagate snake keylogger malware into the victim’s system and capture vital data within it. The malware uses evasive tactics to avoid detection that infiltrates the system to support the attack formulation.
According to the research over the past decade, nearly half of the malware that was detected was using office formats. Office formats are used as they are familiar and all-pervasive applications. Even though PDF is used as a phishing lure it uses the word to deliver the ultimate payload (the snake keylogger). The keylogger is developed using .NET and is capable of stealing sensitive information Including saved credentials, logging victims’ keystrokes, screenshots, and clipboard data as stated by the resource.
The campaign
The campaign was unusual as it was a new pdf-based threat campaign that tactically set itself out to pose as an important document. The PDF was documented as “REMITTANCE INVOICE.pdf” and was sent as an attachment via email. The document seemed skeptical as it was loaded with several evasive functions such as embedding malicious files, loading remotely hosted exploits, and shellcode encryption.
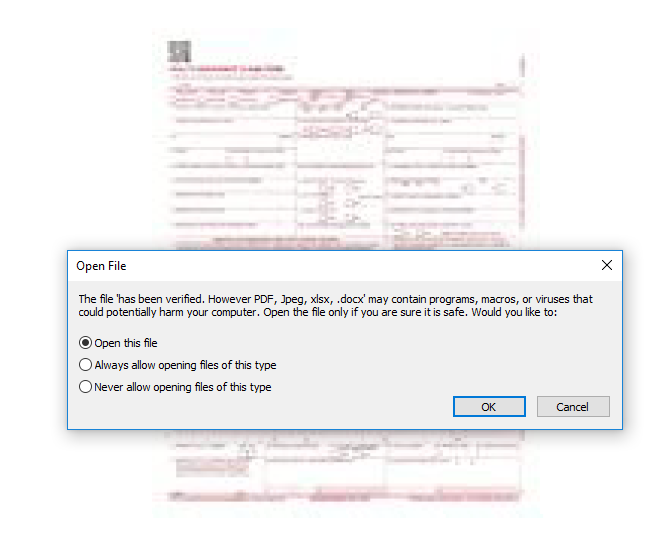
The victims were sent the attachment via email. As the victim opens the file, an ominously named word document opens instead of a pdf document. The attackers set out a bait asking the target to open the file suggesting that the file was a part of the Adobe Reader prompt.
The researchers concluded that the .docx file was an EmbeddedFile object stored within the PDF file which downloads a .rtf file when the protected view is disabled in the word document that was downloaded before. The .rtf file consisted of a ‘document.xml.rels’ file which had URLs hidden within it. However, the action decoded that these malicious embedments were not downloaded from the legitimate domain of the official documents.
Through the research, it was discovered that if the victim connects to the URL given in the document, it redirects the user to download a f_document_shp.doc file which consists of revealed shellcode exploit CVE-2017-11882 which is a remote code executing (RCE) vulnerability in equation editor.
The equation editor is auto-installed with the office package and is used to insert and edit complex equations as Object Linking and Embedding (OLE) items in the word document.
In one of the OLE objects, shellcode was stored and structured in OLENativeSTREAM format. The code so stored was used to decrypt a ciphertext that consisted of other shellcodes which when executed leads to an executable that loads the keylogger.
Measures to avoid getting infected
The keylogger malware is capable of extracting and exfiltrating user data within the system and from the browsers too. As is it capable of completely misusing the user data certain measures like avoiding emails with files attached or website links that come from unknown, suspicious addresses, and updating patching software must be done to avoid getting infected by such malware.
Basic security measures can be taken by users themselves, like using 2 step verifications, installing, and using encryption or anti-malware software. Likewise, users can also perform basic steps to detect the malware where they can check the task manager for any suspicious application running or conduct a full malware scan on their system.
While Office formats remain popular amongst hackers, this campaign demonstrates how hackers are weaponizing PDF documents to infect systems. The attackers utilize various tactics to hide malware, including embedding files, loading remotely hosted vulnerabilities, and encrypting shellcode. Even though such campaign malware attachments are normally done using office format it was unlikely how PDF documents were used to infect the system. Although the exploited vulnerability in this campaign is almost four years old, it is still being used, indicating that the exploit is still viable.