Safety guidelines for government issued email

Nepal Government, in a surprising move, has made provisions for all government employees to be issued official email address (of the form *@mail.nepal.gov.np) and has mandated its compulsory use for all government offices and employees. This statement comes as a government directive named “Government entities email management directives 2075”. While a step in the positive direction, pursuing this endeavour ignoring all its complexities and gravity can end up causing some serious harm. If proper preparations are not made and this project is rushed then it will surely end up resulting in a colossal mismanaged mess. We can take a clue from what a disaster the Aadhar system implemented in India has wrought up. The repeated data breaches and the inefficiency of Aadhar is a result of rushing the implementation without proper preparations and considerations of complexity. A similar fate will surely befall this project too if it pursues the same hurried implementation. While we do not intend to discourage this plan, we just wanted to be a voice of caution so that it shall not cause havoc in the future.
We consider it imperative that before enacting this genuinely praiseworthy act, some critical requirements be completed. Providing proper security training to employees before providing them the email addresses and mandating its use is one of such requirements. Preparing a detailed guideline and usage policy and providing them to all the employees is also a important requirement. We have prepared a basic security guide which might inform them of secure computer and online usage practices.
Use secure and strong password
A secure password must be longer than 8 characters and must contain a mix of number, symbols and, uppercase and lowercase letters. But as these passwords can be hard to remember, you can create password using long phrases or sentences like “1 Bird in Hand & 2 in the Bush”. These types of password are the preferred as they are long, complex and unguessable but still easy for you to remember. You must avoid using personal information that is known to others in your password. You should never use the same password for multiple websites. You should never provide your password to anybody.
Store your password safely
You should never write down or store your password where other can find it. Turn off the password saving feature in your browser. Using password managers is recommended if you find it hard to remember your passwords. They can also help you generate secure passwords. Some popular and trusted password managers are lastpass, keepass, 1password etc.
Be careful while logging in to your email from other’s computer
You must avoid using any other computers than the one assigned to you to access your email account. But, if it becomes necessary then use private windows or incognito mode to login to your email. You can use the shortcut “ctrl+shift+p” to open private browsing mode in Mozilla Firefox, Microsoft Edge and Internet Explorer, and use “ctrl+shift+n” to open incognito mode in Google Chrome. In these modes, none of your data is stored by the browser. Remember to logout after your work is complete or if you are using private browsing mode than closing the private or incognito window shall suffice.
Be wary of phishing attempts
If any emails, website or links redirects you to a legitimate appearing login screen for some website, don’t enter your username and password in the page. See the URL bar to make sure the URL begins with https:// and has a green lock beside it. The images below show how these websites should appear in Chrome and Firefox
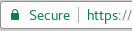
_chrome_
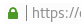
_Firefox_
Then review the address itself, if you’re logging into the official government issues email, make sure that the url has .gov.np at the end. For any other services not following the links is the best protection measure as, URLs can be spoofed using unicodes known as punycode which make two different addresses look exactly identical. It is common practice for attackers to use web addresses that appear in order to fool people and steal their credentials.
Be aware of spoofed emails
Email addresses can be easily spoofed that means attackers can use legitimate email addresses to send mails in order to steal information so, if you receive emails claiming to be official and ask for sensitive information, access to your account or for your password, report them to the authorised IT administrator immediately. Verify the authenticity of any email that seem legitimate before giving away any information by contacting the relevant department. Attackers can also use social engineering tricks like making official appearing calls in an attempt to steal information so you must also be wary of such calls.
Be cautious in regards to attachments and downloads
You should install anti-virus software in your computers and update it regularly. You should never download anything unless you completely trust the source and the file that you’re about to download. If you receive suspicious attachments in the mail report them to your IT administrator and consult them before downloading it. You should also keep your computer and all of the programs up to date.
Do not give access to your computer
You might see pop-ups while browsing the Internet or receive emails stating that your PC is infected and you must clean your PC. These false claims tell you to install some remote access software in order to provide access to your PC over the Internet. You should never do so and when you encounter such messages you should ignore them and exit the website. These messages may seem like below
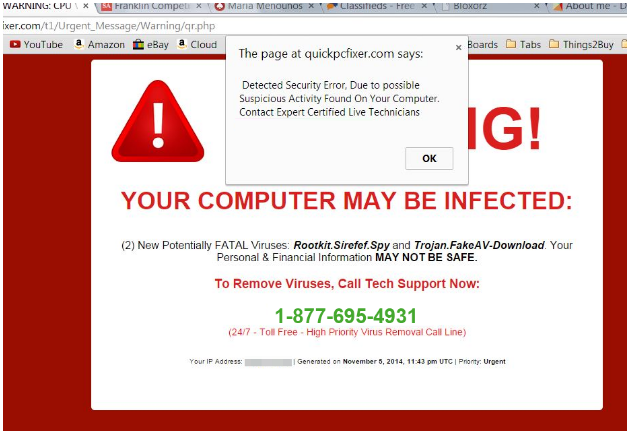
And if someone you know is asking to use your computer, do not let them use it unsupervised. It is best to switch to guest user account before allowing anybody to use your computer.
Use two factor authentication (2FA) where possible
Two factor authentication (2FA) is a security measure where you use secure channel like texts and code generators to generate secure codes which are required in addition to your password for logging into an account. These remove the security risk of someone stealing or guessing your password in order to login to your accounts.