SHARPEXT: A Malware that Compromises Browser Extensions to Steal User’s Email Data

SHARPEXT is a malicious browser extension that has recently been used by a threat actor (SharpTongue) to target several systems. The malware has the capability to scale as it increases its target number of browsers from Google Chrome to the other two browsers, Edge and Whale, and increases the potentiality of being harmful to several other systems. The analysis presented by Volexity stated that a VBS script created by the attacker manually installs SHARPEXT. Before delivering SHARPEXT, the attacker manually exfiltrates the files needed to install the extension from the compromised machine.
The malicious browser extension files, configuration files, and scripts(pow.ps1 and dev.ps1) are loaded as support files for the malware. The first script (pow.ps1) that is performed, ends the active browser process and replaces the “Preferences” and “Secure Preferences” files with ones that are downloaded from the command-and-control (C2) server. The Secure Preferences file, which holds the user’s personal information, will replace the current configuration when Chromium-based browsers are started if the Preferences files do not match the loaded configuration. Further, to prevent manual editing of the Secure Preferences file, a valid “super_mac” value is used.
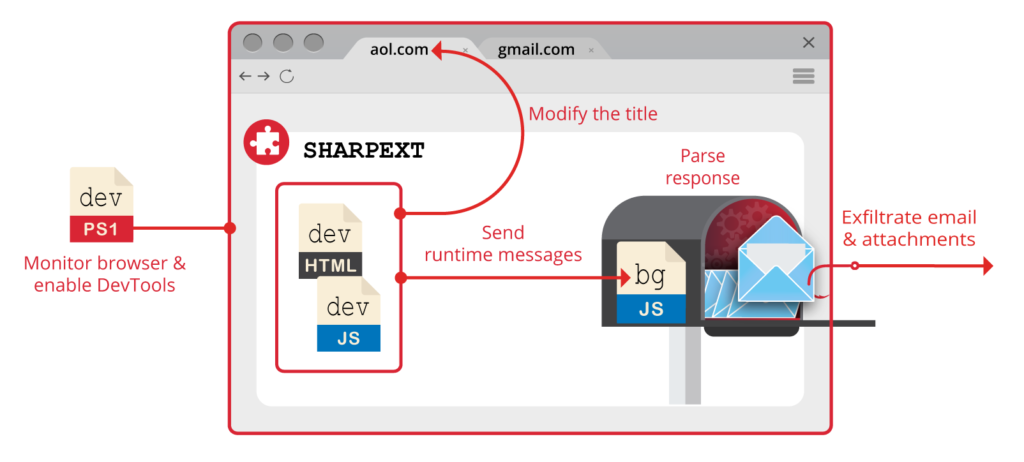
The attacker uses a copy of the resources.pak file, user S-ID values, and the original Preferences and Secure Preferences files to create new Secure Preferences and Preferences files which when deployed retain the existing settings and are accepted by the browser. The malicious extension that is present in the folder “%APPDATA%\Roaming\AF” will be immediately loaded by the browser once the updated preference files have been put in place. It mostly depends on the “DevTools” permission selected in the extension’s settings, which is deployed by the installer, dev.ps1.
The dev.ps1 script searches for processes related to the selected browsers in an infinite loop. When the target runs the browser, the script checks the title of the tab with specific keywords depending on the SHARPEXT version where the keywords are inserted into the title by the malicious extension, when the tab or the pages are changed. Additionally, the script uses the ShowWindow() method and the SW_HIDE flag to hide this window while continuously checking to see if it is present.
The purpose of the DevTools module is to send two types of messages (inspect and packet) to the chromium listeners. The C2 server houses the majority of the code. At the point of execution, it is downloaded and passed to an eval() statement, allowing the attacker to dynamically update the extension code.
SHARPEXT can maintain knowledge of its current state and prevent duplication of stolen data with the use of the information stored in the global variables, such as email addresses to ignore, emails already stolen, monitored tabs, and previously exfiltrated attachments.
This evolving attack has the capability to steal thousands of emails from multiple victims with its deployment, which can be mitigated through generic detection and investigation. PowerShell ScriptBlock logging can be used to identify and sort malicious activity. Furthermore, it is recommended to use YARA rules to detect the related activity and block the IOCs that are listed.