Sophisticated ‘DarkTortilla’ Crypter

DarkTortilla is a .NET-based crypter that works by delivering numerous malicious payloads, with the potential to inject illegal content into the user system with the ability to manipulate both users and sandboxes to believe that it is benign. Originally designed to keep malicious payloads hidden from detection software, DarkTortilla has recently gained the capability to deliver remote access trojans (RATs) and information stealers like AgentTesla, AsyncRat, and target payloads like Cobalt Strike and Metasploit. DarkTortilla is also noteworthy for its anti-tamper controls that ensure both the processes used to execute the components in memory are immediately rerun upon termination.
Working
Typically, DarkTortilla is distributed via email spam and spear-phishing attachments carrying .dmg, .iso, .img, .tar, or.zip attachments that contain archives with an executable for an initial loader that is used to decode and launch a core processor module. This executable may be embedded within the archive itself or downloaded from text storage websites.
As it is highly configurable and complex, the crypter can also be used to deliver add-ons and additional payloads, decoy documents and executables, and retrieve data from public sites such as Pastebin, Textbin, and Paste. Furthermore, it can be configured to display a fake message box, perform anti-VM and anti-sandbox checks, and achieve persistence, to migrate execution to the ‘temp’ folder, process add-on packages that were downloaded initially, and migrate execution to its installation directory.
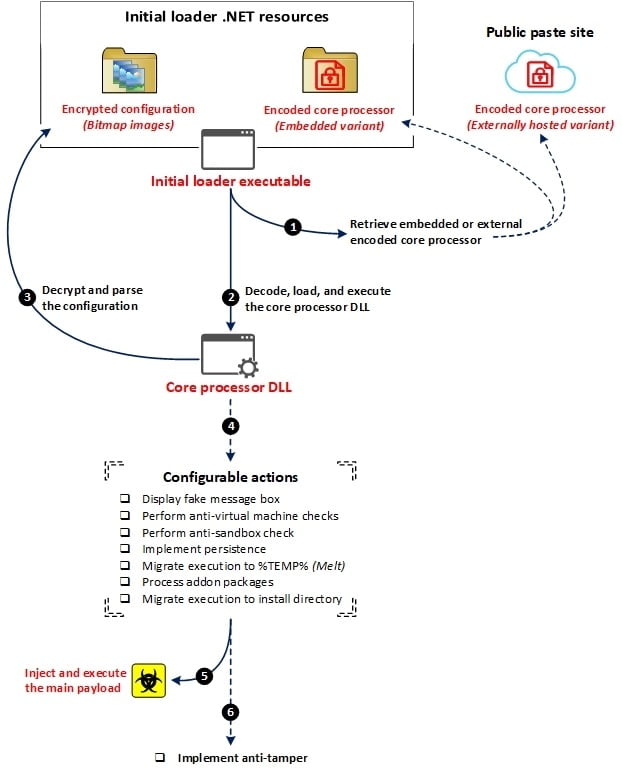
The core processor is to establish persistence and inject the primary RAT payload into memory without leaving a trail on the file system through an elaborate configuration file that allows it to drop packages, including keyloggers, clipboard stealers, and cryptocurrency miners.
Anti-tampering and Anti-analysis
Its anti-tamper controls make sure that both of the processes used to run the memory-based components are immediately restarted after termination. To avoid tampering with the execution of DarkTortilla or the payload, it injects its payload within the context of the configured sub process and applies anti-tamper controls. The anti-tampering feature makes it difficult to remove from a setting and ensures its persistence. Because the malware’s primary payload is executed from memory, there will be no evidence of the payload on the filesystem. To avoid being analyzed, a code obfuscator was used, which altered namespace, class, function, and property names that were specially crafted to make it very difficult for the de compiler that needs multiple samples to be combined to actually understand the code.
Difficult to Detect
DarkTortilla migrates execution to the Windows %TEMP% directory during initial execution, which allows attackers to gain the capability to allow DarkTortilla to hide in an infected system, which makes it difficult for the defenders to detect.
One of the most prevalent cases of dark tortilla use is the case where the malware was seen leveraging a Microsoft Exchange RCE vulnerability (CVE-2021-34473) to execute malicious PowerShell within customer environments that allowed attackers to bypass authentication, impersonate an arbitrary user, and write an arbitrary file to achieve remote code execution.
Overall, Dark Tortilla can be described as a crypter, which is software designed to encrypt, obfuscate, and manipulate malware, as stated earlier, making it difficult for security programs to detect. It can be configured with a variety of payloads, support a variety of persistence types, can show the victim’s customizable message delivery options, and migrate its execution to avoid detection.
References
https://www.secureworks.com/research/darktortilla-malware-analysis