Threat Report 2018, Nepal – TL;DR

As with last year, Threat Nix has continued in its effort to assess the state of security of Nepali cyberspace with its annual Threat Report. Threat Report 2018 attempts to present even bigger picture of cybersecurity in Nepal compared to Threat Report 2017 published last year. The report includes study of some key indicators of security practices, awareness and implementations, trying to cover as much Nepal owned IT infrastructure as possible. With ever increasing attempts of cyber attacks and cyber warfare emerging as the new norm, it is essential to be more vigilant of our cyberspace. With more and more aspects of life being digitised, utmost attention should be kept on security and making sure that cyber attacks of any scale, small to large, cannot disrupt the day to day tasks.
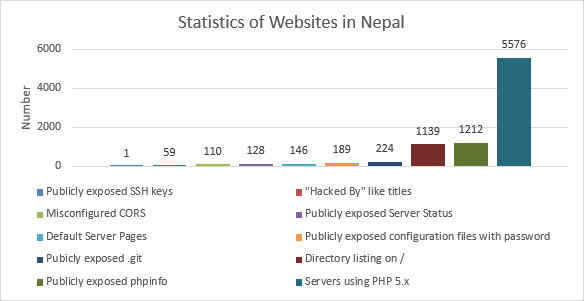
Threat Report 2018 contains statistics regarding website security, misconfigurations, easily hackable devices and services, presence of common vulnerabilities and much more. In addition, we also collected credential dumps of various data breaches and searched for emails of .np cctld and well known Nepali corporate domains within these dumps. We scanned Nepali websites to see if they are serving malicious content or hosting phishing pages and found a sizable number serving such contents.
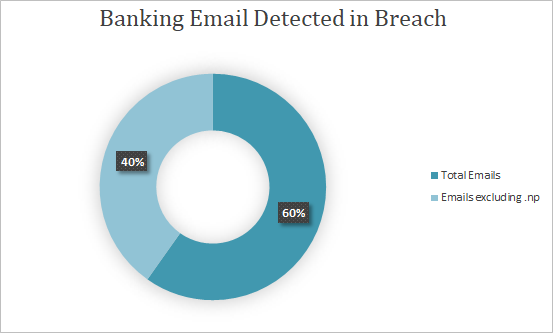
In our research regarding the effect of international data breaches in Nepal, we found that 8378 (.np) Nepali emails had their credentials dumped from various websites. What’s more shocking is that most of these were official email addresses from corporate organisations and even government offices and were used to register accounts in various websites even porn and dating websites. These dumps are readily available for download and according to the Verizon Data Breach Report (DBIR), such compromised credentials are the primary causes of most data breaches.
So, if any of the leaked email addresses have access to critical infrastructure and have reused the dumped passwords, then the critical systems can be easily compromised. Furthermore, we found that a majority of the users were using common and weak password such as 123456, password1, abcdef and even easily guessable password like their name, mobile number, location etc. This depicts the general lack of awareness regarding security and the importance of using strong password.
Similarly, observing the use of .np domains for malicious purpose, we found 222 websites being used for nefarious purpose. While 213 of these domains were used for social engineering and phishing, 9 Nepali domains were used for distributing malware. This raises the question about the trustworthiness of websites and how can we trust any Nepali websites when even government and organisations website are being used for phishing and malware distribution.
While researching the status of website security in Nepal we scanned Nepali website for common misconfiguration. From the research we found that many websites had made common misconfigurations that allowed public access to sensitive informations that can even allow the complete takeover of the websites. While it is not much surprising to find such misconfigurations in small organisations and personal websites, it is shocking to see such serious misconfigurations in critical websites of high value organisations and financial institutions. We found a large portion of Nepali websites that are still using PHP 5.x which has reached its end of life and is no longer receiving any updates. We expect this to cause some serious issue in 2019 as no security patches will be available for the current vulnerabilities as well as the critical vulnerabilities that will definitely be discovered over time.
During our research, we also found that databases, network devices and services were exposed to the internet with either default password and some even with no password at all. Many of the services were very sensitive in nature and the databases even contained large amount of sensitive user and organisational data. Even more insecure were the client devices like routers and IP cams. We found that a majority of these devices were accessible with default credentials. This shows that cyberspace in Nepal is not that secure as a result of lack of awareness and negligence in part of related personnels in both private and government sectors.
Threat Report does show reduced number of cybersecurity incidents in Nepal 2018 comparing with 2017. While this result projects a positive trend towards security in Nepal, we still have to see if this is due to improvement in security or due to reduced hacking attempts overall. Still, this decrease in the number of incidents is a hopeful indication of growing security awareness. But, considering the number of increase of vulnerable and misconfigured devices, hosts and websites, we should not be surprised to see an increased number of incidents in the future. The presented findings and statistics show that there is still much of a way to go in creating secure Nepali cyberspace. We also see the need of awareness among all the involved stakeholders which consist of government policymakers to general end users regarding cybersecurity and the safe usage of Internet and computer technologies.
We hope this report will find its way to policy makers, security administrators, and general users and will help them in better understanding the status of security. Threat Nix expects this report to be a force for change and improve the security status of Nepali cyberspace in order to create a cyber-secure Nepal.
You can read the full Threat Report 2018 at https://threatnix.io/reports/2018/