UnRAR Vulnerability: A file-write flaw that can lead to RCE
A path traversal security vulnerability was discovered in the UnRAR binary, which when exploited can result in remote code execution (RCE) on the commercial email platform Zimbra, as well as other software. UnRAR is a utility that belongs to the RARlab and is a 3rd party tool used in Zimbra. The UnRAR utility works as a spam checking and virus scanning tool for RAR archives. It has been assigned CVE-2022-30333 and has a base score of 7.5. The vulnerability was disclosed by a vulnerability researcher at Swiss security firm Sonar.
In terms of the technical aspect, Zimbra consists of pre-configured software that is used to send and receive emails and has the UnRAR feature to detect spam and scan for viruses. The vulnerability is triggered while receiving an incoming email with attached RAR files that use the UnRAR utility to extract the content to a temporary directory.
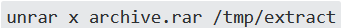
While processing the email through the server, unrar is used in many instances. But for the specific scanning purpose, software (Amavis) is used in Zimbra’s mail service, which works by default to ensure that all files are safely deleted after processing them through UnRAR.
UnRAR is used as it has the capability to prevent symbolic link(symlink)attacks on both Windows and Unix. Some examples of relative and absolute payloads for symlink attacks are: “../../../tmp/shell” on Unix or “..\..\..\tmp\shell " on Windows.
In this process, the UnRAR’s ability to detect symlink attacks is negated by using a typical vulnerability pattern where untrusted data is modified after it has been validated. Attackers can take advantage of this behavior since it converts all backslashes (\) to forward slashes (/). This function allows an attacker to write a file anywhere on the target filesystem.
When an application or victim user extracts an untrusted archive, it allows the attacker to create files outside of the target extracted directory and further exploit it, leading to giving the attackers access to every single email sent and received on a compromised email server. The only requirement for this attack is that UnRAR must be installed on the server, which is expected given that it is needed for virus scanning and spam-checking on RAR archives.
As aforementioned, if the file-write primitive helps to create and overwrite files in the working directories of other services and extract content to a known location, they will most likely be able to use it to execute arbitrary code on the system. An attacker can achieve RCE and will have the ability to leverage the backdoor login functionality and steal credentials of an organization’s users who are using the Zimbra mail server. It is most likely that they can escalate their privileges to extract more sensitive data from the internal services of an organization.
It’s worth noting that the vulnerability affects any software that uses an unpatched version of UnRAR to extract untrusted archives. An attacker could leverage the vulnerability to gain full control of an email server and even use it to access or modify other internal resources within the organization’s network through pre-authenticated remote code execution.
Workaround
Security patches by RarLab for UnRAR are available in source code version 6.1.7, included with the binaries of version 6.12. Any previous version may be vulnerable, so it is recommended to upgrade the software and use the latest versions of UnRAR, even if the organization’s web server and mail server are not on the same physical machine. While downloading or if it has already been downloaded, it is recommended to check if the repository contains the patched version or not. If not, it is suggested to download it directly from RarLab’s website.
References
https://blog.sonarsource.com/zimbra-pre-auth-rce-via-unrar-0day/
https://thehackernews.com/2022/06/new-unrar-vulnerability-could-let.html