Retiring Malicious Macros
What are macros?
Simply stating, macros are Microsoft programs or instructions that can be used to automate repetitive tasks in any of the Microsoft office programs or applications. The use of office macros to initiate attacks as an initial threat vector has been increasing throughout the decade. One of the main reasons threat actors used macros was because they are very strong and adaptable and because they can host VBA code. Visual Basic for Applications (VBA) is mainly a type of command that can create or automate repetitive word and data or processing functions that help generate customized forms, reports, and graphs in Microsoft applications. Moreover, the main purpose of having VBA was to help developers build user-defined functions to manipulate user interface features like menus and toolbars.
These functionalities have been used as an attack vector to instigate several attacks. The macros are replaced with malicious macros that represent themselves with similar functionality and take up action in the system. These Macro malwares hide themselves in Microsoft Office files and are delivered as email attachments or inside ZIP files. These files use names that are intended to entice or scare people into opening them. They frequently resemble invoices, receipts, legal documents, and other documents and, additionally, are sophisticated enough to replace prompt commands and launch the Microsoft Word document with other office applications.
However, some of the recent campaign data presented by Proofpoint showed that the use of VBA and XL4 Macros decreased by approximately 66% from October 2021 through June 2022 after Microsoft announced that VBA macro auto-blocking in downloaded Office documents. When a user has actively enabled macros in Office applications, threat actors use VBA macros to automatically run malicious content. XL4 macros are unique to the Excel program but can also be used by threat actors. Typically, threat actors distributing macro-enabled documents rely on social engineering mostly phishing methods to convince a recipient that the content is important and that enabling macros is necessary to view it. Since Microsoft blocked them, threat actors have pivoted away from macro-enabled documents attached directly to messages to deliver malware and have increasingly used container files such as ISO and RAR attachments and Windows Shortcut (LNK) files.
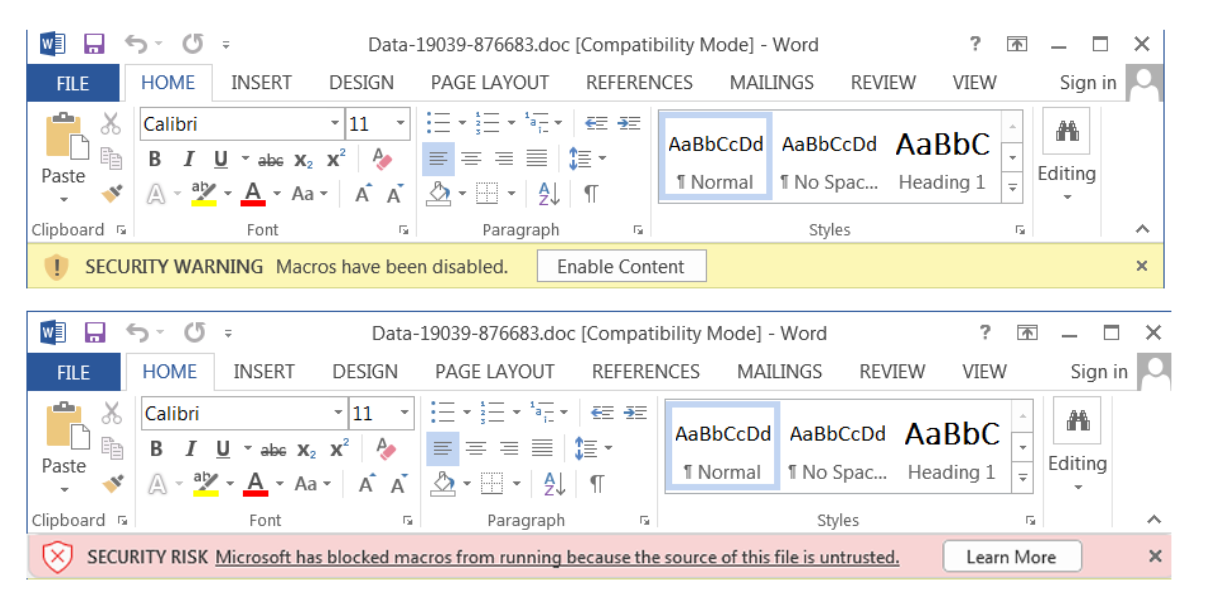
How risky were macros?
Typically, threat actors embed a malicious macro within an Office document and send it along with phishing emails. The office displays a security warning stating that macros have been disabled when victims open the lure document. By default, Office disables all macros and prompts the user to enable them manually. In most cases, threat actors include a banner or a picture in the document instructing the recipient to enable macros in order to view the document correctly. If a victim falls for this, the macros will typically run Windows shell processes such as PowerShell or WScript to download the second-stage payload.
But now, threat actors are shifting away from documents with macro functionality and using more diverse file types for initial access after Microsoft macros were disabled. But instead, they will be using different container file formats to deliver malware while relying less on macro-enabled attachments. These modifications are forcing the adaptation of ISO and other container file formats, such as LNK files, which can get around Microsoft’s macro blocking security measures and make it easier to distribute executables that can result in ransomware and follow-on malware, data eavesdropping, data theft, and other malicious activities.
Mitigation
Malware, working around the attachment, has the largest effect on the threat landscape in the present and in the future, but can be remediated with alert and detection mechanism implementations. Just as mentioned in one of the reports presented by security researchers at Logpoint, organizations must avoid the use of macros altogether. The administrators should make sure that the audit and logs are formatted in such a way that they can satisfy the requirements while configuring them in deployed detections. All in all, as they are rapidly evolving, all users must stay enticed to general technics to mitigate malware such as updating the system, avoiding downloading files and documents from the internet, applying security filters in emails, and using anti-virus.
References
https://www.proofpoint.com/us/blog/threat-insight/how-threat-actors-are-adapting-post-macro-world